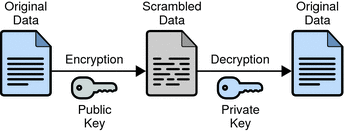
Public-Key Cryptography
Cryptography is useful for safeguarding blockchain wallets.
Wallets are used to store digital assets, including cryptocurrencies, non-fungible tokens (NFTs), or any other items created and transferred on the blockchain.
When users create a wallet, they get a public key and a private key. The private key is to your wallet what a password is to your bank account. Every transaction must be signed with a private key to prove ownership of the assets.
The existence of a private key means that no one can gain access to your wallet and move funds and other assets without your approval.
20
79 reads
The idea is part of this collection:
Learn more about crypto with this collection
The differences between Web 2.0 and Web 3.0
The future of the internet
Understanding the potential of Web 3.0
Related collections
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates