15+1 Ways to Hack-Proof your Smartphone
Curated from: unboxingspace21.blogspot.com
Ideas, facts & insights covering these topics:
23 ideas
·45.3K reads
192
6
Explore the World's Best Ideas
Join today and uncover 100+ curated journeys from 50+ topics. Unlock access to our mobile app with extensive features.
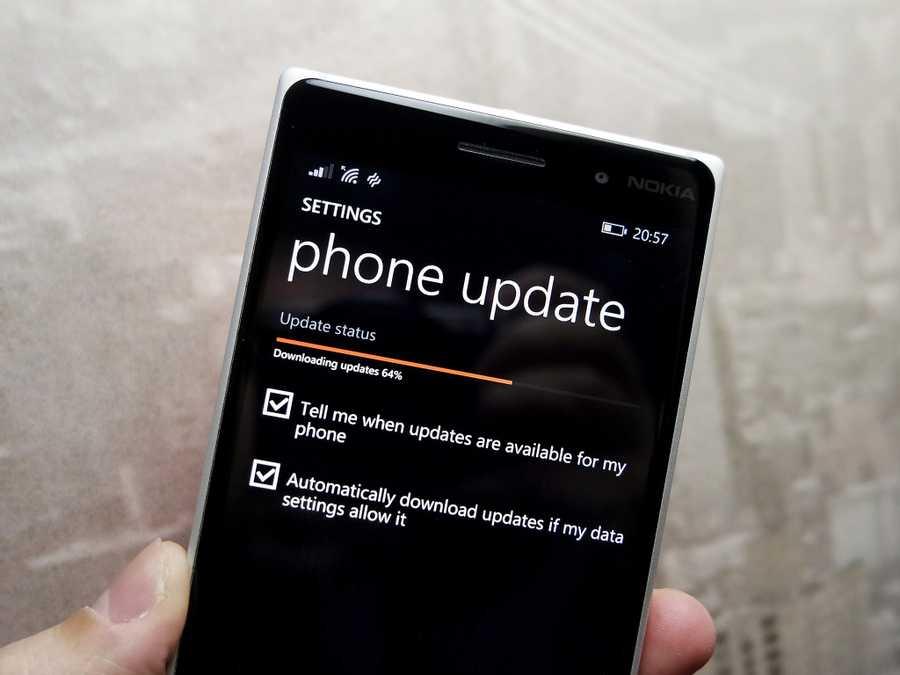
1. Keep up to date – and don’t open up holes yourself:
When it comes to protecting yourself against hackers, step one is always to install software updates as soon as they become available: that’s as true on smartphones as it is on computers. Yes, updating can be a tiresome and intrusive process, and it sometimes brings annoying changes to the interface that you’re used to. All the same, a huge proportion of successful hacks exploit vulnerabilities that have already been patched; exposing yourself unnecessarily is just daft. I’d also strongly
362
4.65K reads
2. Be careful of what you install:
When you install a smartphone app, you may be asked to grant it various permissions, including the ability to read your files, access your camera or listen in to your microphone. There are legitimate uses for these capabilities, but they’re potentially open to abuse: think before you approve the request..
350
3.37K reads
3. Review what’s already on your phone:
Even if the apps on your phone seemed simple and safe when you installed them, subsequent updates could have turned them into something more sinister. Take two minutes to review all the apps on your smartphone, and see which permissions they’re using: on iOS, you’ll find lots of relevant information under Settings > Privacy. On Android, it’s harder to get an overview of which apps have which permissions.
355
2.98K reads
4. Make it hard for intruders to get in:
If a thief gets physical access to your phone, they can cause all sorts of trouble. For a start, your email app probably contains a trove of personal information. Make sure your phone is locked when not in use: both Android and iOS can be set to require a six-digit passcode. Your device may offer other options too, like fingerprints or facial recognition.
Such methods aren’t perfect – a really determined hacker could copy your fingerprints from a drinking glass, or trick a camera with a photograph of you
344
2.67K reads
5. Be prepared to track and lock your phone:
Plan, so even if your phone is stolen, you know your data is safe. One option is to set your phone to automatically erase itself after a certain number of incorrect attempts to enter the passcode. If that seems a bit drastic, don’t forget that both Apple and Google operate “find my device” services that can locate your phone on a map, and remotely lock or erase it.
353
2.61K reads
6. Don’t leave online services unlocked:
Auto-login is a very convenient feature, especially since a virtual keyboard can make typing passwords a chore. It’s also a huge liability: an intruder simply needs to open your browser to gain access to all your online accounts. Ideally, therefore, you shouldn’t use auto-login features at all. If you must, use a password manager app that requires you to regularly re-enter a master password. And don’t use the same password for more than one app or service.
349
2.37K reads
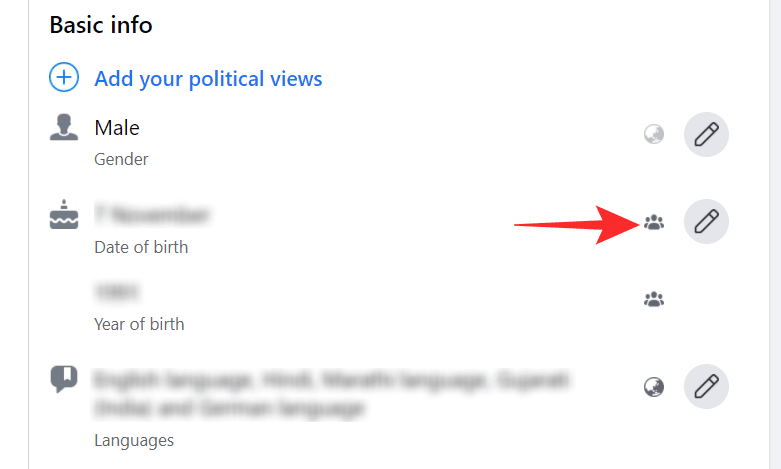
7. Adopt an alter ego:
If you’ve followed this advice so far, it should be very difficult for anyone to get into your phone. However, some major hacks have been pulled off without any access to the victim at all. If someone can find out (for example) your date of birth, hometown, and mother’s maiden name – all stuff that can be easily picked up from a site like Facebook – that’s often all they need to reset a password and start breaking into your accounts.
Personal information can easily be gleaned from sites such as Facebook.
352
2.58K reads
8. Beware of open wifi:
We all know there’s a risk involved in using an open wireless network. But you may not realize how severe it is: anyone in the vicinity can snoop on what you’re doing online. This sort of attack demands specialist software and skills, so it’s unlikely to be a hazard in your local cafe, but it’s not a danger that can be ignored. If you’re at all doubtful about a wireless network, don’t connect – stick with your phone’s mobile internet connection. Or use a VPN tool such as CyberGhost or TunnelBear
353
1.85K reads
9. Lock individual apps:
A strong passcode helps keep thieves out of your phone, but what if a stranger snatches your phone while you’re using it? Or asks to borrow it to check a website, then bolts off down the street? On Android, as a second line of defense, you can lock individual apps, so even if someone can get past your lock screen, they can’t open your email or banking app without a second password. This capability isn’t built into the OS, but there are plenty of free apps that provide it, such as AVG AntiVirus Free.
347
1.62K reads
10. Get a warning when your phone goes walkies:
If you’re on the fence about investing in a smartwatch, here’s a little-known feature that could swing it: Apple Watch and Android Wear devices can warn you immediately if they lose Bluetooth contact with your phone. If you get this notification while you’re in a public place, there’s a good chance someone’s just picked your pocket and is currently making off with your phone. The device will normally be less than 50 meters away when the connection drops, so the warning gives you a chance to ring the phone right away
343
1.89K reads
11. Keep an eye on things behind the scenes:
No matter how cautious you are, you can’t completely eradicate the danger of your phone being hacked – not unless you refuse to install any apps or visit any websites. What you can do is supplement your on-device security measures with an online service. LogDog – available for both Android and iOS – is an app that monitors your identity on sites such as Gmail, Dropbox, and Facebook. It alerts you to suspicious activity, such as logins from unfamiliar places, giving you a chance to step in and change your credentials before serious harm can be done.
352
1.69K reads
12. Keep Your Tracking and Remote Locking Settings On:
At this stage, we assume that you’ve enabled your mobile’s lock screen feature with a multi-digit passcode, face/fingerprint recognition, or a complicated pattern. This is particularly helpful if you lose your phone or if a thief has gotten their hands on your device. But if you think that your screen lock will make it impossible for thieves to misuse your phone, you’re not aware of the tricks hackers can use to bypass the phone’s initial security mechanism. There are ways to bypass even fingerprint lock and facial recognition security mechanisms!
340
1.45K reads
13. Install Security Software Tools on Your Mobile Device:
Antivirus software and anti-malware software are not limited to computers only. You should use them on your mobile phones as well to protect your phone from hackers. When you surf online, different types of malware (like viruses, trojan horses, worms, etc.) can be installed on your device via malware-loaded websites. Your device also might get infected through malicious email attachments or apps. Security software not only detects and removes malware but also can warn you when you visit a bad site or download a malicious app. Some malware gets downloaded on your mobile without your notice
340
1.22K reads
14. Be Judicious About What You Download and Install on Your Phone:
Not everything is as it appears. Be vigilant when installing apps or downloading images, videos, files, songs, email attachments, etc. from the internet.
336
1.66K reads
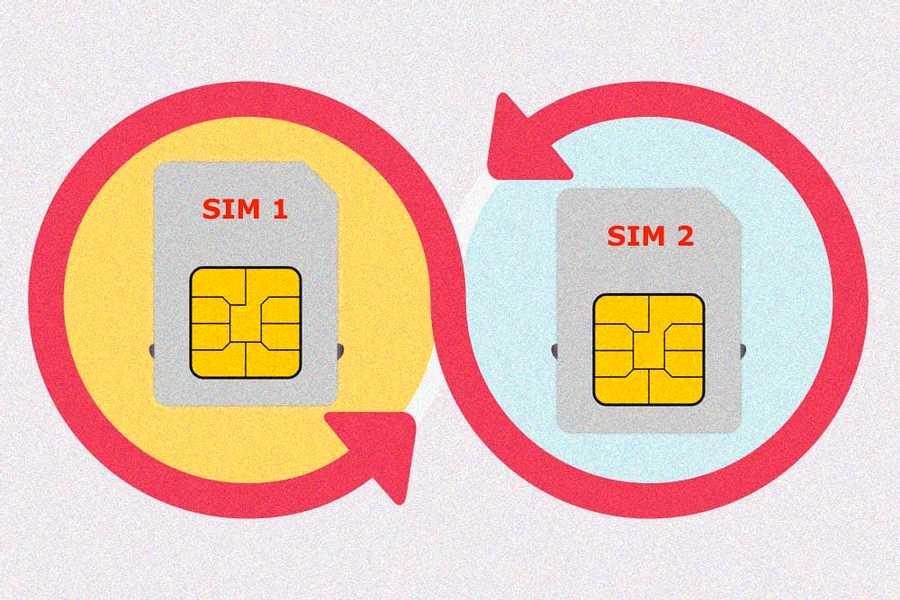
15. Protect Yourself from SIM Swapping:
SIM swapping occurs when a bad guy calls your mobile service provider and asks for a replacement SIM card. This unauthorized SIM swapping is possible when a hacker has access to some of your confidential information (such as the last four digits of your social security number, or any identity proof document) and uses it as part of their social engineering scam.
If they’re successful in convincing your mobile provider to port your number, the attacker can intercept all your phone calls, SMS text messages, and potentially gain access to all accounts and services that are linked to your number
340
1.43K reads
Disable the “Allow Siri When Locked” function.
Go to Settings > Siri and Search > Disable the Allow Siri When Locked feature**.** In the past, some bugs in the iPhone allowed anyone to bypass the screen lock and access a couple of functions using Siri.
337
1.59K reads
Password protects your cloud storage apps.
This includes apps such as Google Drive, Google Docs, iCloud, etc. Check out these resources for more information on how to protect your iCloud account and how to protect your Google Drive and docs.
339
1.33K reads
Disable the “smart unlock” feature.
Some mobile devices have this feature, which automatically unlocks your phone when you are at a “safe” location (home, work, etc.) or when your smartwatch is nearby. But it’s very risky because the attackers can bypass the lock screen authentication if they are in near proximity.
334
1.2K reads
Password protects important files, folders, and apps from getting an additional layer of security.
Use Apps like Folder Lock (available for both Android and iPhones) for this purpose.
342
1.44K reads
Avoid using public charging ports.
Hackers can compromise charging ports (this is known as juice jacking) to intercept the data and break into your device.
342
1.45K reads
Avoid jailbreaking devices.
Jailbreaking (or rooting) means making unauthorized changes in the default device settings using some software. People jailbreak their phone to unlock it (change service providers), use banned or pirated apps, customize the looks, or enable tethering (hotspot) service without paying an extra fee. But when you jailbreak your phone, you not only void the device’s warranty but also weaken the phone’s security posture. Hackers can easily insert malware and steal confidential data from a jailbroken phones
334
1.18K reads
Appeal
Hope You Enjoyed reading & Got some Impact-full Learnings from this article, If you Did then Hit the like button. This helps us to work harder & Smarter Day by Day. & it motivates us to make this kind of content...
330
1.24K reads
IDEAS CURATED BY
Hi, Readers we are Unboxing Space here we do all kind of Tech videos, Unboxing, Review, Tips & Tricks, Information & so many interesting things. To watch our videos you can SUBSCRIBE to our channel & Blog so you don’t Miss any informative thing. by IGDM
Unboxing Space's ideas are part of this journey:
Learn more about technologyandthefuture with this collection
Understanding machine learning models
Improving data analysis and decision-making
How Google uses logic in machine learning
Related collections
Similar ideas
4 ideas
How can you protect your Mobile phone from the Hackers?
shubhamsocio.blogspot.com
3 ideas
The Best 2FA Apps 2021: Authy vs Google Authenticator
cloudwards.net
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates