Monitor Fraudulent Activities
Fraudsters aim to find weak links and vulnerabilities in your business systems from where they can stage their attack.
To strengthen your business from fraud, you need to know the methods that fraudsters use, which part of your security system to strengthen, and which tools to use to fend off scammers.
6
50 reads
The idea is part of this collection:
Learn more about technologyandthefuture with this collection
How to develop a growth mindset
How to think creatively and outside the box
How to embrace change
Related collections
Similar ideas to Monitor Fraudulent Activities
The Reasons To Read More
- Reading is our moral duty: We read because knowledge is power. We become weak and are easily manipulated if we don’t read.
- Reading is a way to see the future: The truth is old and preserved in most classic books, which is rehashed and repackaged in...
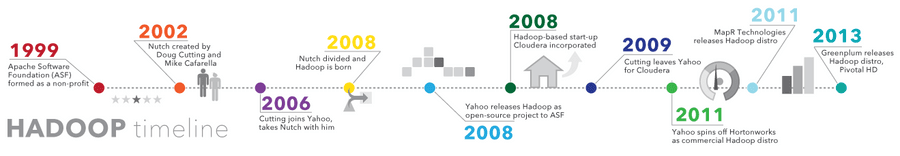
Big data Hadoop
- Ability to store and process huge amounts of any kind of data, quickly. With data volumes and varieties constantly increasing, especially from social media and the Internet of Things (IoT) , th...
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates