Communication and Quantum Technology
Curated from: medium.com
Ideas, facts & insights covering these topics:
10 ideas
·431 reads
2
Explore the World's Best Ideas
Join today and uncover 100+ curated journeys from 50+ topics. Unlock access to our mobile app with extensive features.
Communication And Quantum Technology
The development of communication technologies paved the way for man’s fourth stage of evolution and marked the onset of a new era driven by technology and versatile digital developments. The growth of humanity in computer advancements has led to innovative solutions to our everyday difficulties and has helped us introduce solutions for even the most complex problems. The field of communication is affected the most by these developments.
9
79 reads
Continued...
Today, the world is facing a cyber-attack every 2 seconds. In this context, the demand to secure one’s data has become the top priority of individuals and companies connected with cyberspace. Various methods have been introduced in the past, to help secure communication technology. However, there have always been cases that force us to reconsider the possibility of complete security.
8
59 reads
Cyber Attacks And QKD
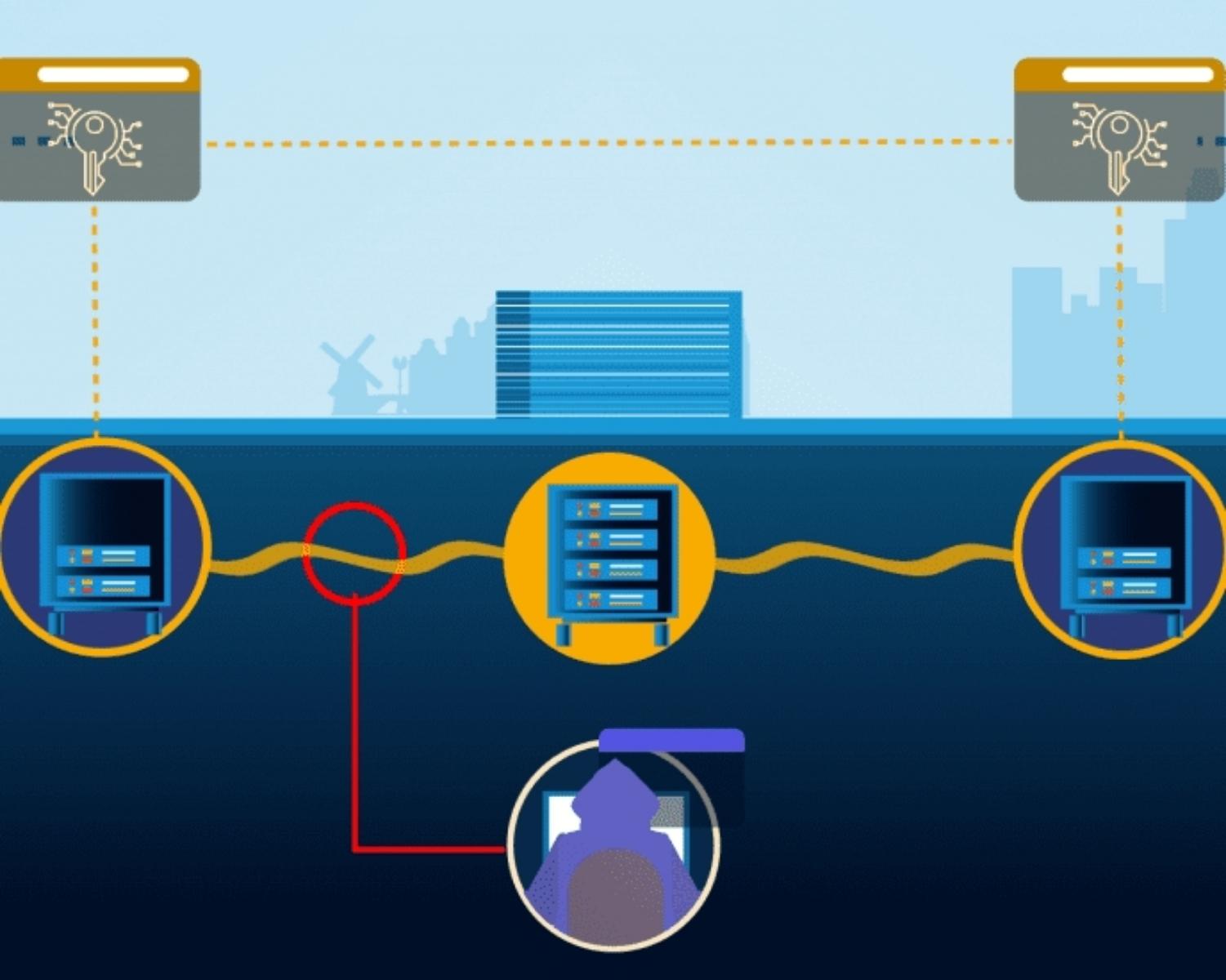
The security of voice calls can be compromised with ease as the radiations and communication waves between 1 cell phone tower to another can be tapped and the information can be intercepted by a malicious person. To tackle the problem of leakage of information through voice calls the concept of linking communication technology to quantum cryptology was theorised.
8
44 reads
What is Quantum Technology?
Quantum technology is an emerging field of physics that is based on the principles of quantum mechanics. The word quantum in physics is defined as the minimum amount of any physical entity or property involved in an interaction between particles. This interaction of particles of two or more entities forms the foundation of quantum cryptology.
8
53 reads
Quantum cryptography and communication.
The laws of quantum physics allow the photons or light particles to be in a state of superposition i.e., represented in multiple combinations of binary digits (0 and 1) at an instant in time. These combinations are termed qubits .
In classical cryptography, hackers use brute force to identify private keys from the public key to decrypt important data. However, in quantum cryptology, we deal with Quantum Key Distribution (QKD) process where keys are symmetrical and are randomly generated in real-time making them virtually un-hackable.
8
47 reads
QKD and defence
The security of encrypted data solely depends on the strength of the key used to encrypt that information. The mathematical complexity along with the permutations and combinations that the keys have undergone decides how easy it is to decrypt the data. Due to the complex and random nature of keys that are generated through the Quantum Key Distribution process, quantum cryptography is being considered as a mode of communication between the authorities responsible for the defence and safety of a country.
8
41 reads
Trial Conducted By DRDO
In December 2020, DRDO of India conducted successful trials of QKD to showcase secure communication. The Quantum-based security solution against eavesdropping was validated at a 12-km range and 10 dB reduction over the fibre optic channel.
The development of such an incredible technology is indeed a remarkable achievement.However,the said technology is miles away from seeing widespread usage across the globe.A crucial reason behind this anomaly is the lack of exploration and knowledge regarding the depths of Qalong with the absence of required tools to perform the above-mentioned exploration.
8
25 reads
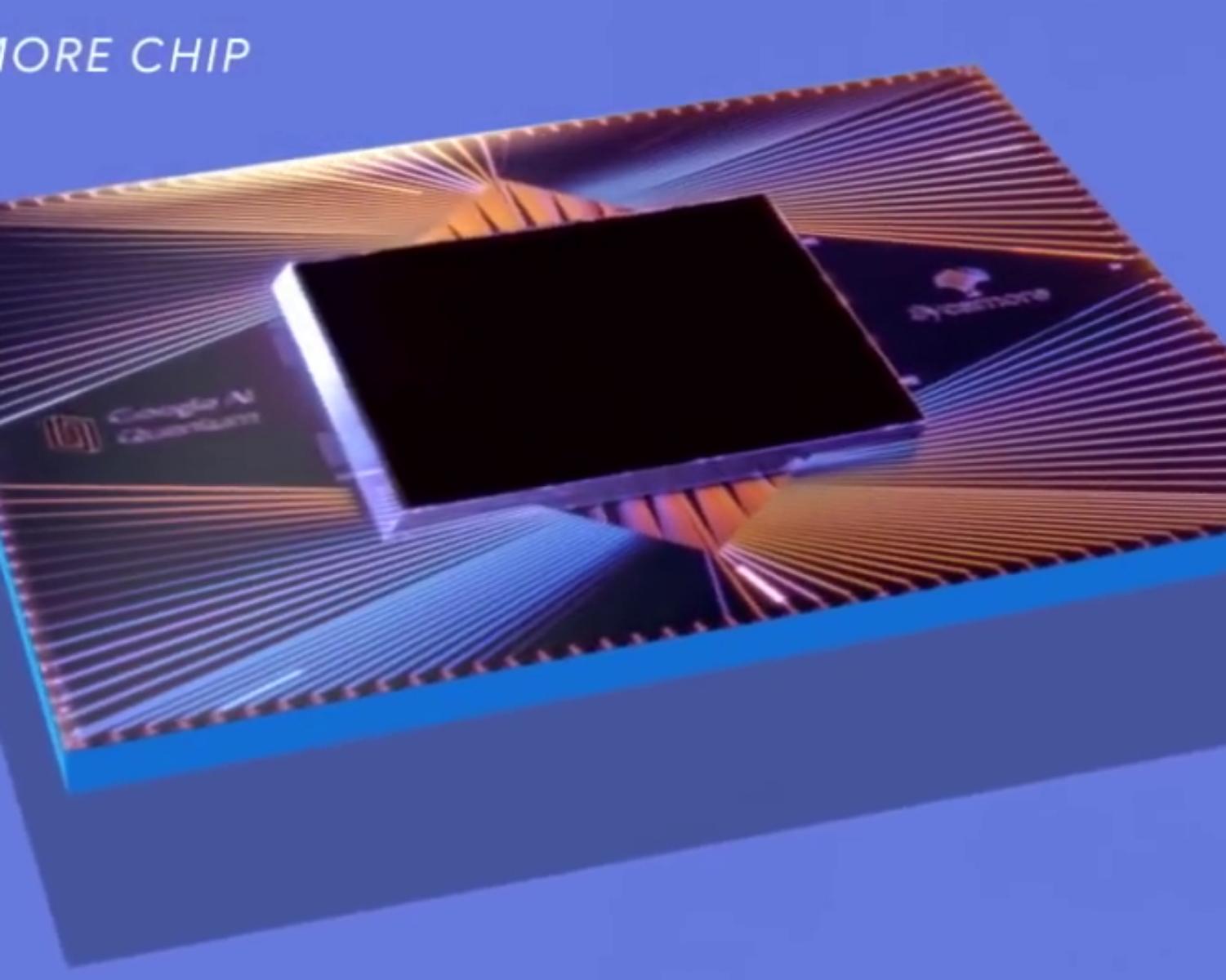
Processor Sycamore's Achievement
The negligence of people regarding the security of communication technology is also a reason why the mass production of devices that can help us combine quantum cryptography with information security is still a problem that is to be solved by tech giants and innovators.
In October 2019, Google introduced its 53-qubit processor Sycamore , a quantum computer that performed a complex calculation within 3 minutes 33 seconds or 200 seconds which would have taken the world’s most powerful supercomputer 10,000 years to compute.
8
25 reads
Conti
The introduction of powerful machines had made it mandatory to introduce solutions to the risk they shadow upon our private information, making the development of quantum cryptography the need of the hour.
8
32 reads
What is Quantum Key Distribution?
QKD is a way to secure the network from code-breaking even by a quantum computer which ensures the information is safely transferred from one point to another without any eavesdropping or tapping into the information.
The encrypted data is sent as classical bits (0s and 1s) but the keys are generated concurrently and are then sent in the quantum state to avoid the person trying to access the information and decoding the data.
8
26 reads
IDEAS CURATED BY
卐 || एकं सत विप्रा बहुधा वदन्ति || Enthusiast || Collection Of Some Best Reads || Decentralizing...
अर्हम् Arham's ideas are part of this journey:
Learn more about personaldevelopment with this collection
Ways to improve productivity
Strategies for reducing stress
Tips for managing email overload
Related collections
Similar ideas
10 ideas
What Is a Digital Signature? | Binance Academy
academy.binance.com
2 ideas
JPMorgan unveils research on quantum resistant blockchain network
cointelegraph.com
6 ideas
What Is Cryptocurrency? Everything You Need To Know
daydreamerlive.com
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates