Explore the World's Best Ideas
Join today and uncover 100+ curated journeys from 50+ topics. Unlock access to our mobile app with extensive features.
What Differentiates the World's Most Successful Companies?
The world’s most successful companies all exhibit some form of structural competitive advantage: A defensibility mechanism that protects their margins and profits from competitors over long periods of time.
5
48 reads
The Power of the Network Effect
A good part of the most successful companies leverage the power of the network effect as their competitive advantage.
Network effects occur when the value of a product or service is subject to the number of users. A positive network effect means that a product or service becomes more valuable to its users as more people use it.
5
28 reads
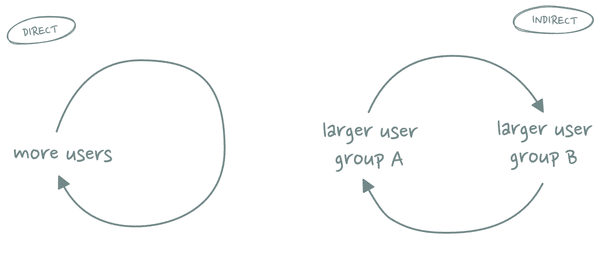
Types of Network Effect
There are several types of network effect that should be properly understood:
- Direct network effects: they occur when the number of users has a direct impact on the value of a product.
- Indirect network effects: they occur in two-sided (or multi-sided) products where the size of one user group affects how valuable the product is to another user group.
- Data network effects: describes products which become better with more users via the data those users generate.
5
17 reads
Switching and Multihoming Costs
Switching costs describe how difficult or expensive it is for a user to switch from one product to another.
Multihoming costs explain how easy or likely it is to use multiple competing networks simultaneously.
In general, the higher the switching and multihoming costs, the more defensible a network typically becomes.
5
19 reads
Atom-based Network Effect Businesses
Telephone and railroads companies are more defensible than companies such as Facebook and Google because their business mainly relies on atoms instead of bits.
In contrast to bits, atoms have marginal costs. You can copy and paste a piece of software at virtually zero cost, but producing an additional piece of hardware has all sorts of marginal costs associated with it. This means that atom-based network effect businesses have switching and multihoming costs.
5
12 reads
The Idea of Value Chains
Value chains are horizontal visualizations of all the value-adding business activities involved in creating a product or service from start to finish.
Value chains are great to analyze traditional businesses and industries but they are not a very useful framework for tech companies.
5
14 reads
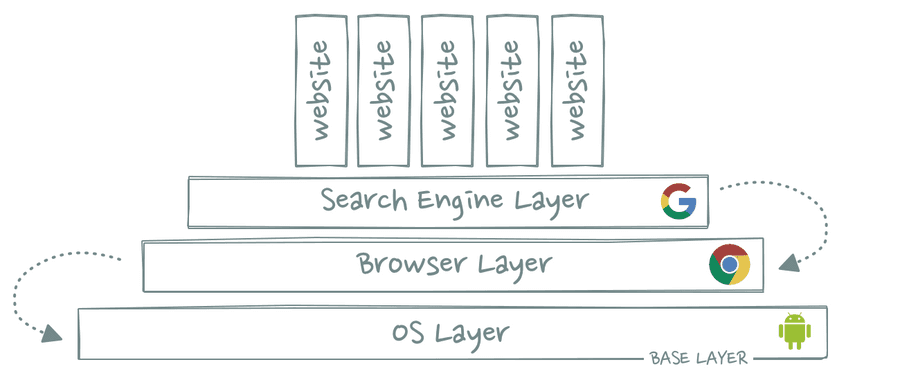
The Vertical Stack
If you want to understand the power dynamics between different platforms, aggregators and other players in a tech ecosystem, it’s better to look at them as a vertical stack with different layers.
On each layer of the stack, companies are trying to create value and to capture value. The lowest layers of the stack are typically the most powerful. If you are able to take control of a layer, you can dictate the terms of most of the value creation and value capture that is happening in the layers above you.
5
13 reads
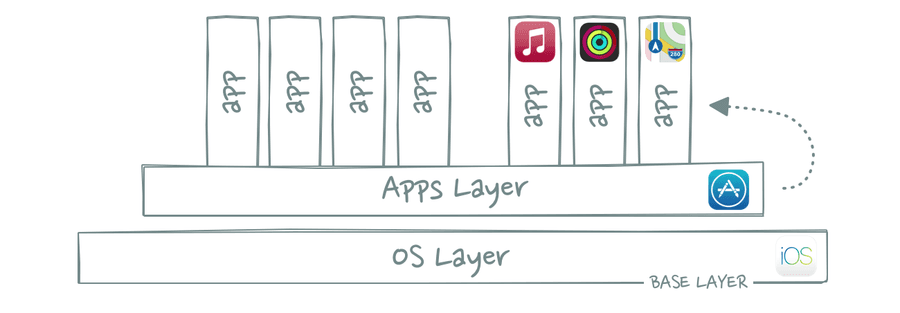
What Companies Do?
As a result of the vertical stack, companies are trying to:
- Create layers on top of their business (everyone wants to be a platform)
- Move down the stack to get closer to the base layer (to increase defensibility)
5
11 reads
The Base Layer
The base layer is the final interface between the stack and the end user – which is typically an operating system tied to a piece of hardware.
5
13 reads
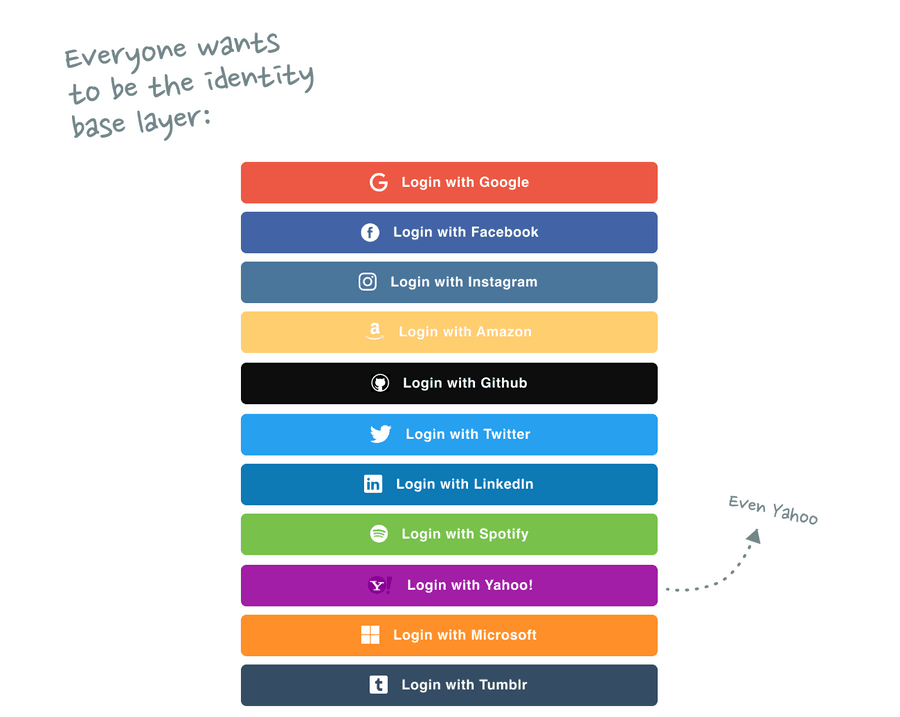
The Identity Layer
But what if the end of the stack isn’t an interface? What if the lowest possible layer in the stack is actually the user itself?
Identity is a crucial component of almost every single layer in the stack. Every network is just a collection of nodes and if you want to build connections between those nodes you need an identity layer. Even in a pseudonymous network, each user has a consistent identifier.
Unsurprisingly, dozens of companies are trying to become the default identity layer.
5
16 reads
IDEAS CURATED BY
Software engineer by 🌞 and sleepyhead by 🌑. Software architecture. Distributed systems. Personal productivity. Cats.
CURATOR'S NOTE
We all know that, the more a product is used, the more it will be used. The problem is that, our understanding of this phenomenon is quite limited. What if we tried to better understand the dynamics behind it? This article is a great read for anyone that would like more insights on this interesting topic.
“
Riccardo Busetti's ideas are part of this journey:
Learn more about cybersecurity with this collection
Understanding the basics of blockchain technology
The benefits and challenges of using blockchain
The future of blockchain technology
Related collections
Similar ideas
5 ideas
The Product Strategy Stack
ravi-mehta.com
6 ideas
Why Decentralization Matters
onezero.medium.com
23 ideas
15+1 Ways to Hack-Proof your Smartphone
unboxingspace21.blogspot.com
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates