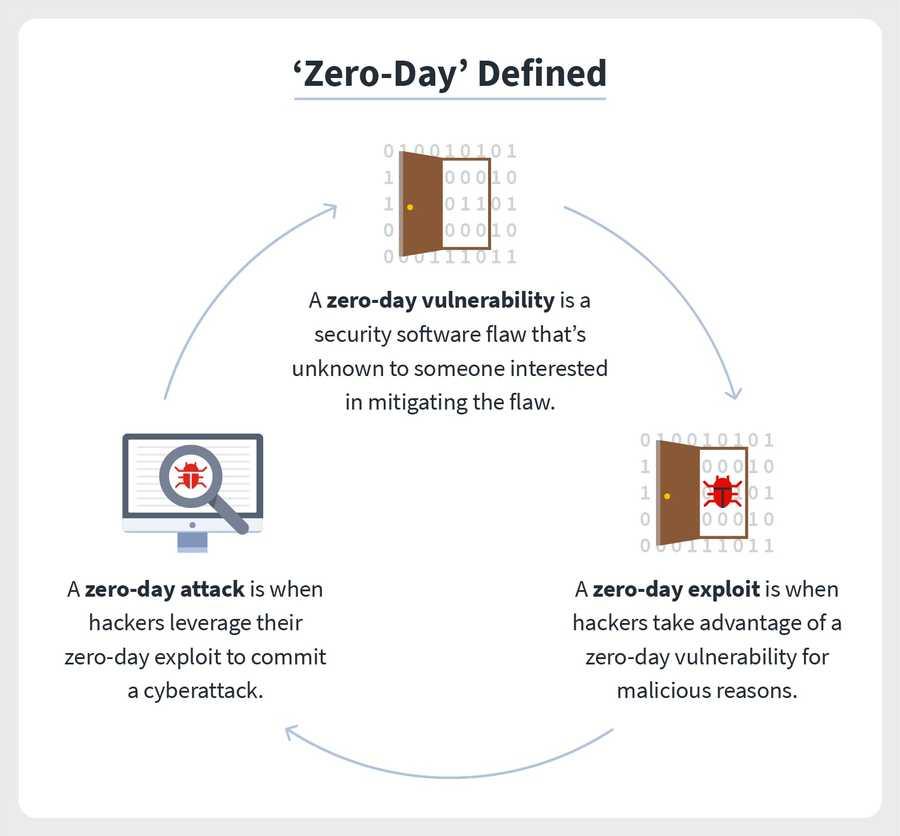
1. Zero-day definitions:
The term “zero-day” refers to a newly discovered software vulnerability and the fact that developers have zero days to fix the problem because it has been — and has the potential to be — exploited by hackers. Sometimes written as 0-day, zero-day definitions run the gamut: A zero-day vulnerability, also known as a zero-day threat, is a flaw in security software that’s unknown to someone interested in mitigating the flaw, like a developer. A zero-day exploit is when hackers take advantage of a zero-day vulnerability for malicious reasons, oftentimes by way of malware to commit a cyberattack.
77
1.19K reads
CURATED FROM
Zero-day vulnerability: What it is, and how it works
unboxingspace21.blogspot.com
15 ideas
·7.61K reads
IDEAS CURATED BY
Hi, Readers we are Unboxing Space here we do all kind of Tech videos, Unboxing, Review, Tips & Tricks, Information & so many interesting things. To watch our videos you can SUBSCRIBE to our channel & Blog so you don’t Miss any informative thing. by IGDM
Nowadays it is important to be aware of this kind of thing, So just Trying to add Value...
“
The idea is part of this collection:
Learn more about cybersecurity with this collection
How to build trust in a virtual environment
How to manage remote teams effectively
How to assess candidates remotely
Related collections
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates