Zero-day vulnerability: What it is, and how it works
Curated from: unboxingspace21.blogspot.com
Ideas, facts & insights covering these topics:
15 ideas
·7.61K reads
31
Explore the World's Best Ideas
Join today and uncover 100+ curated journeys from 50+ topics. Unlock access to our mobile app with extensive features.
1. Zero-day definitions:
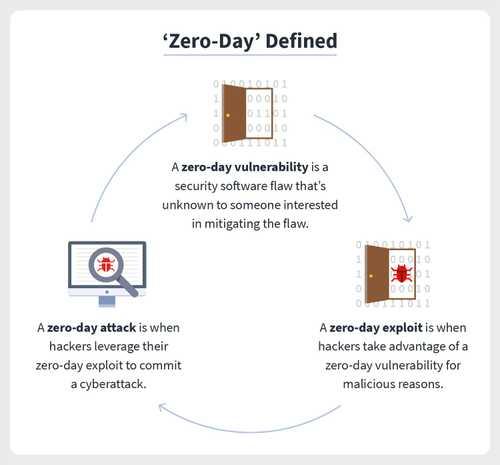
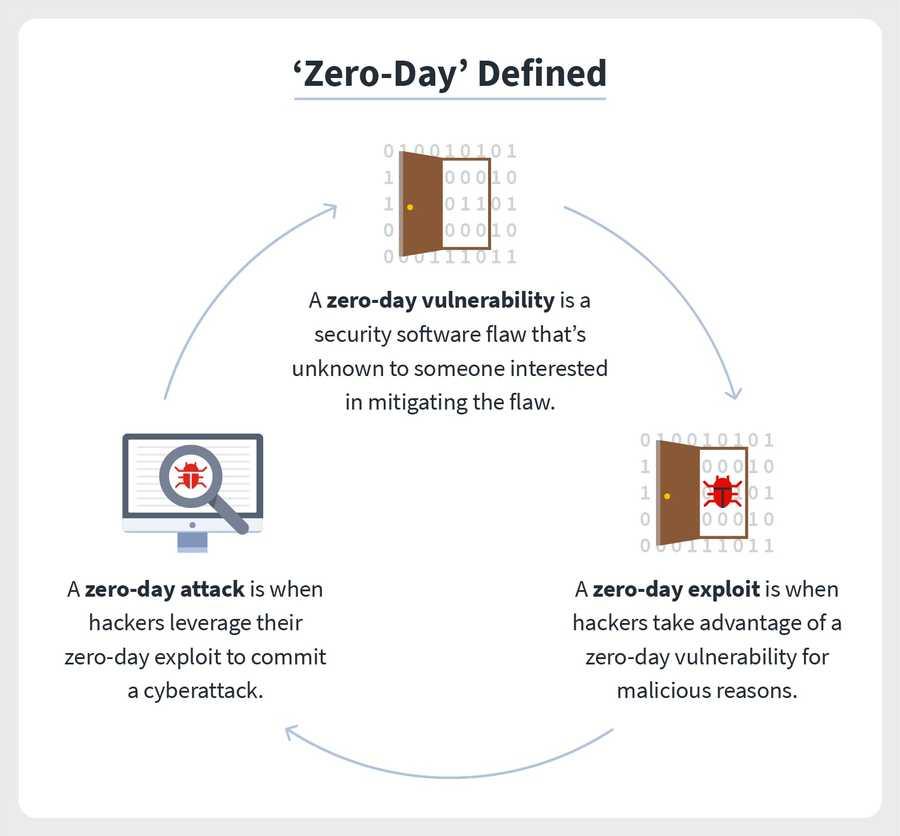
The term “zero-day” refers to a newly discovered software vulnerability and the fact that developers have zero days to fix the problem because it has been — and has the potential to be — exploited by hackers. Sometimes written as 0-day, zero-day definitions run the gamut: A zero-day vulnerability, also known as a zero-day threat, is a flaw in security software that’s unknown to someone interested in mitigating the flaw, like a developer. A zero-day exploit is when hackers take advantage of a zero-day vulnerability for malicious reasons, oftentimes by way of malware to commit a cyberattack.
77
1.19K reads
2. What makes a vulnerability a zero-day?
Security software vulnerabilities can come in many forms, including unencrypted data, broken algorithms, bugs, or weak passwords. What makes a vulnerability a zero-day is when someone interested in mitigating the flaw is unaware of it, meaning an official patch or update to fix the flaw doesn’t exist. Once the vulnerability is discovered, it is no longer considered a zero-day.
66
875 reads
3. How do zero-day attacks work?
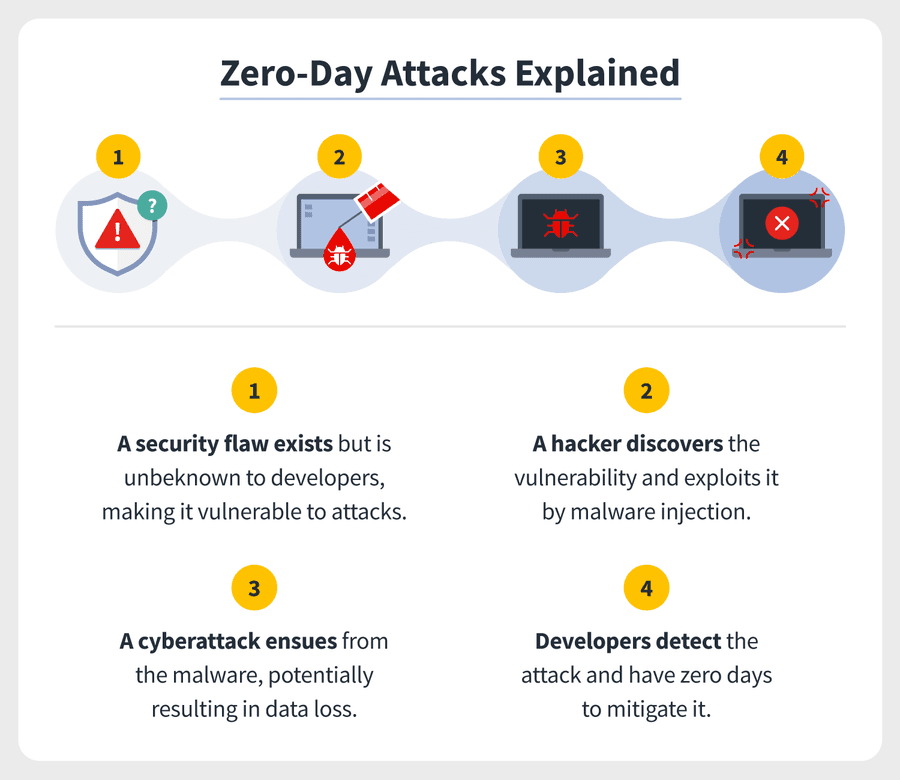
Zero-day attacks begin with zero-day vulnerabilities, meaning flaws or holes in security software. These can result from improper computer or security configurations or programming errors by developers themselves. The whole notion of a zero-day attack is that cyber attackers exploit these vulnerabilities without developers knowing. Cyberattackers might write — or purchase from the dark web — exploit codes to spot these vulnerabilities. When they do, it’s akin to a welcome mat for a zero-day attack.
65
675 reads
4. Who conducts zero-day attacks?
While software developers are constantly looking to patch security vulnerabilities we see this in the form of software updates cyberattackers are constantly seeking to exploit them. And there are many types of cyberattackers, each with its own motivations: Cybercriminals or hackers are often financially motivated Hacktivists are motivated by drawing attention to a cause social or political Corporate espionage artists are motivated by spying on companies Cyberwarfare attackers can be countries or independent malicious actors who want to compromise a cybersecurity infrastructure as an act of war
65
537 reads
5. Who are the victims of zero-day exploits?
Victims, including individuals businesses, or organizations government agencies, And if you’re an everyday computer user, a zero-day vulnerability can pose serious security risks because exploited malware can infect operating systems, web browsers, applications, open-source components, hardware, even IoT devices through otherwise harmless web browsing activities. This can include viewing a website, opening a compromised message, or playing infected media.
65
495 reads
6. How to identify zero-day vulnerabilities:
Oftentimes, zero-day vulnerabilities are detected when it’s too late — when they’re exploited, that is. There are some more technical ways to identify zero-day vulnerabilities, including scanning internet traffic, examining codes of incoming files, and leveraging malware detection methods. For everyday computer users, antivirus software can take out some of this guesswork for you. What’s more, avoiding zero-day exploits and vulnerabilities from the start can go a long way.
66
439 reads
7. How to avoid zero-day exploits and vulnerabilities:
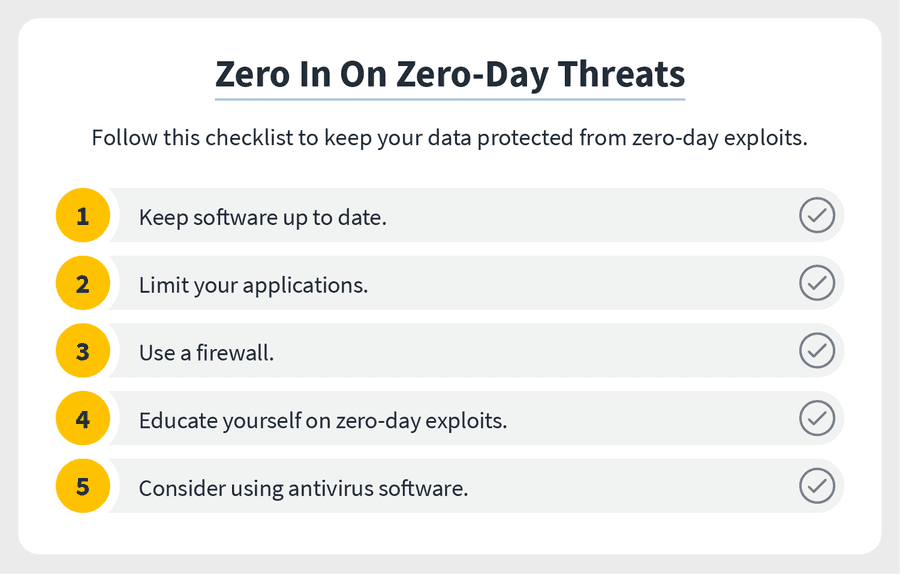
Even as we can’t always detect these vulnerabilities, we can protect our devices and data in the event an exploit does occur. Consider these proactive and reactive security measures. Keep software up to date to ensure security patches are in place and to reduce the risk of malware infection. Limit your applications because the less you have downloaded, the less data you’re putting at risk. Use a firewall to monitor and block suspicious activity, such as zero-day exploits. Educate yourself on zero-day exploits and seek out solutions when zero-day vulnerabilities are discovered.
66
384 reads
8. Examples of zero-day exploits:
inally, don’t underestimate the threat of zero-day exploits. Cybercriminals will seek to exploit security holes and gain access to your devices and your personal information. They can use your information for a range of cybercrimes including identity theft, bank fraud, and ransomware. Just consider these recent and headline-making examples of zero-day exploits.
66
375 reads
Google Chrome, 2021:
Google Chrome fell victim to several zero-day threats, attributed to a bug in JavaScript.
65
412 reads
Zoom, 2020:
Hackers exploited a vulnerability in the video conferencing platform that allowed them to take remote control over PCs.
65
407 reads
Apple, 2020:
A bug in Apple’s iOS software allowed hackers to compromise devices from remote locations.
66
386 reads
Microsoft Windows, 2019:
Government agencies across Eastern Europe saw their Microsoft Windows software exploited, resulting in suspicious apps being installed, data changed, and programs compromised.
66
370 reads
Microsoft Word, 2017:
Individual computer users saw their bank accounts compromised after opening a Microsoft Word document containing zero-day malware.
65
359 reads
Stuxnet, 2010:
A self-replicating computer worm disrupted Iranian nuclear plants, taking control of computers and altering the speed of centrifuges in the plants, ultimately shutting them down.
Stuxnet isn’t only one of the earliest zero-day exploits used, but it’s also one of the most famous. The zero-day attack was even made into a documentary, appropriately titled “Zero Days.”
69
354 reads
Zero-day Malware
zero-day malware or more broadly as a zero-day exploit. And they might deliver this by way of social engineering tactics or phishing. Once the zero-day exploit is downloaded on devices, the zero-day attack is executed. The havoc that ensues can include: Data is stolen Hackers taking remote control of devices Other malware installed Files corrupted Contact list accessed and sending spam messages Spyware installed to steal sensitive information Since zero-day attacks are inherently stealthy, it can take months or even years for these zero-day exploits to be realized.
65
353 reads
IDEAS CURATED BY
Hi, Readers we are Unboxing Space here we do all kind of Tech videos, Unboxing, Review, Tips & Tricks, Information & so many interesting things. To watch our videos you can SUBSCRIBE to our channel & Blog so you don’t Miss any informative thing. by IGDM
CURATOR'S NOTE
Nowadays it is important to be aware of this kind of thing, So just Trying to add Value...
“
Unboxing Space's ideas are part of this journey:
Learn more about cybersecurity with this collection
How to build trust in a virtual environment
How to manage remote teams effectively
How to assess candidates remotely
Related collections
Similar ideas
6 ideas
How to be Safe from Cyber Attacks
unboxingspace21.blogspot.com
Read & Learn
20x Faster
without
deepstash
with
deepstash
with
deepstash
Personalized microlearning
—
100+ Learning Journeys
—
Access to 200,000+ ideas
—
Access to the mobile app
—
Unlimited idea saving
—
—
Unlimited history
—
—
Unlimited listening to ideas
—
—
Downloading & offline access
—
—
Supercharge your mind with one idea per day
Enter your email and spend 1 minute every day to learn something new.
I agree to receive email updates